What Is 2FA Authentication?
Two-factor authentication (2FA) is a security process in which a user provides two different authentication factors to verify their identity. This process adds an extra layer of security to protect accounts and sensitive information because it requires not only a password and username but also something that only the user has on them. This is typically something like a physical mobile device, though other types of 2FA methods also exist.
The primary goal of 2FA is to reduce the risk of unauthorized access to accounts. Even if an intruder gets hold of your password, they are still unable to access your account without the second factor. The second factor can include a variety of things such as:
- Something You Know: This could be an additional PIN or a password.
- Something You Have: This could be a smartphone with an app like Google Authenticator or a hardware token.
- Something You Are: This could be biometric verification, such as a fingerprint or retina scan.
2FA increases the security of online transactions and can prevent breaches that come from poor password management, such as weak passwords, reused passwords, or even stolen passwords. By leveraging 2FA, you add a formidable barrier to entry for would-be intruders, thereby securing your resources more effectively.
Why 2FA Authentication is Important
- Increased Security: The most obvious reason to implement 2FA is the heightened level of security it provides. Cybersecurity threats are constantly evolving, and standard password protection is relatively easy to bypass. 2FA ensures that even if unauthorized individuals get hold of your password, they cannot access your account without the second factor.
- Protection Against Phishing: Phishing is a common method used by cybercriminals to steal usernames, passwords, and other credentials. Even the most savvy users can sometimes fall victim to well-crafted phishing attempts. Because 2FA requires the second factor, it renders stolen passwords practically useless.
- Safe Remote Access: In the modern era of remote work, having secure remote access is crucial. Employees often access sensitive information over various networks that might not be secure. 2FA helps ensure that only legitimate users are granted access, regardless of the network they are on.
- Compliance with Regulations: Many industries are governed by stringent regulations that require robust security measures to protect sensitive information. Implementing 2FA can help your organization remain compliant with laws like GDPR and HIPAA, thereby avoiding potential fines and legal issues.
- Enhanced User Trust: When users know that an organization takes security seriously, their trust increases. 2FA shows that you prioritize the security of user data, which can improve user loyalty and satisfaction.
- Mitigates Impact of Data Breaches: Data breaches are increasingly common and can be devastating both in terms of revenue and reputation. 2FA mitigates the potential damage from a data breach by ensuring that simply knowing a username and password isn’t enough for an attacker to gain access to sensitive information.
- Protects Against Credential Stuffing Attacks: Attackers frequently use automated tools to try combinations of usernames and passwords gleaned from prior breaches (credential stuffing attacks). Even if they have the correct credentials, 2FA will block access without the second factor.
How Does Two-Factor Authentication Work?
- User Enrollment: The user sets up 2FA by linking an authentication method to their account. This could be by scanning a QR code with an authentication app, linking a mobile number for SMS verification, or using a hardware token.
- Login Process Initiation: When the user logs in, they first enter their username and password.
- Second Factor Prompt: After the password entry, the user is prompted to provide the second authentication factor. This could be a time-sensitive code from an authenticator app, a push notification, a one-time password sent via SMS, or biometric verification.
- Verification: The user inputs the second factor, which is verified against what is stored or generated in real time. For example, an authentication app generates new verification codes every 30 seconds based on a secret key shared during the setup process.
- Access Granted/Denied: If the second factor is correct, the user is granted access to the account. If it is incorrect, access is denied, and additional security measures may be initiated, such as sending an alert to the user or locking the account temporarily.
Using Authenticator Plugins
Google Authenticator Plugin
- Install the Google Authenticator Plugin:
- Go to your WordPress admin dashboard.
- Navigate to
Plugins->Add New. - In the search bar, type
MiniOrange 2-factor authentication. - Click
Install Nowand thenActivate.
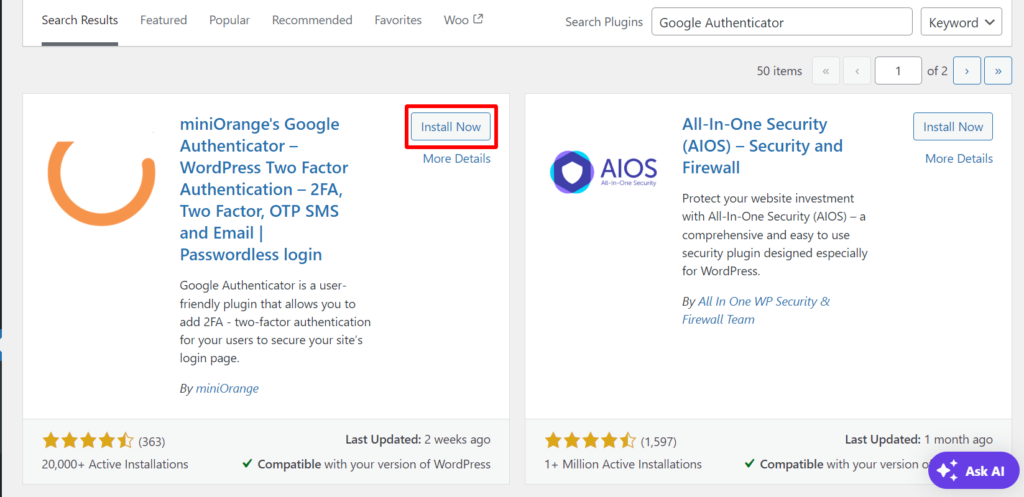
- Configure MiniOrange 2-factor authentication:
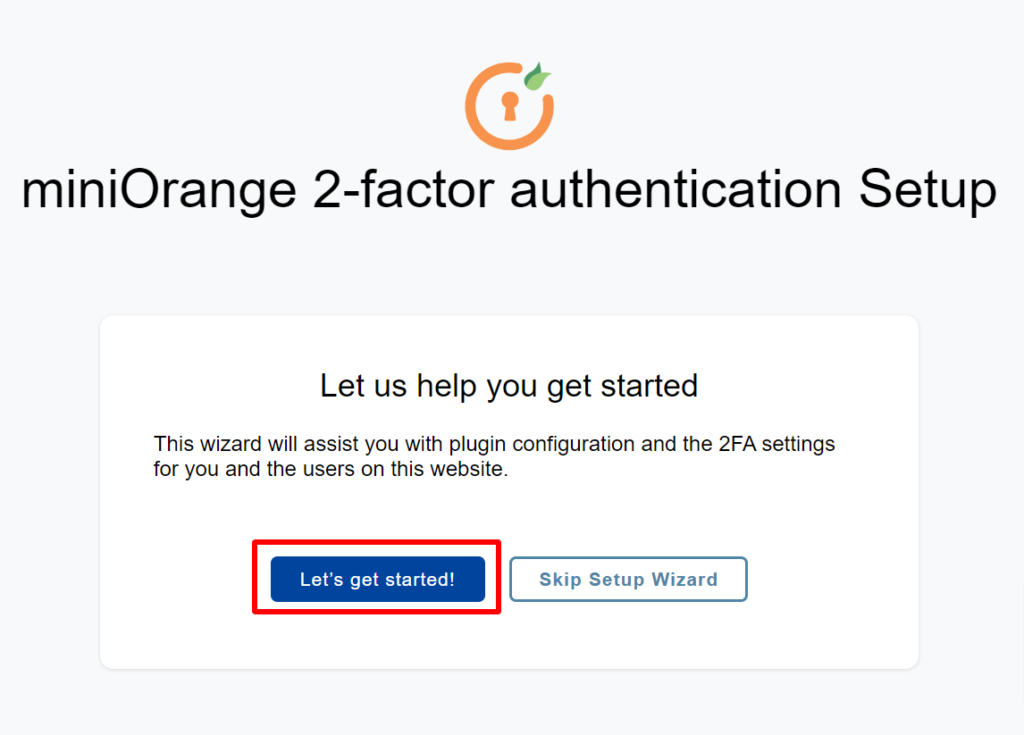
- Click Let’s Get Started then you get a setup page
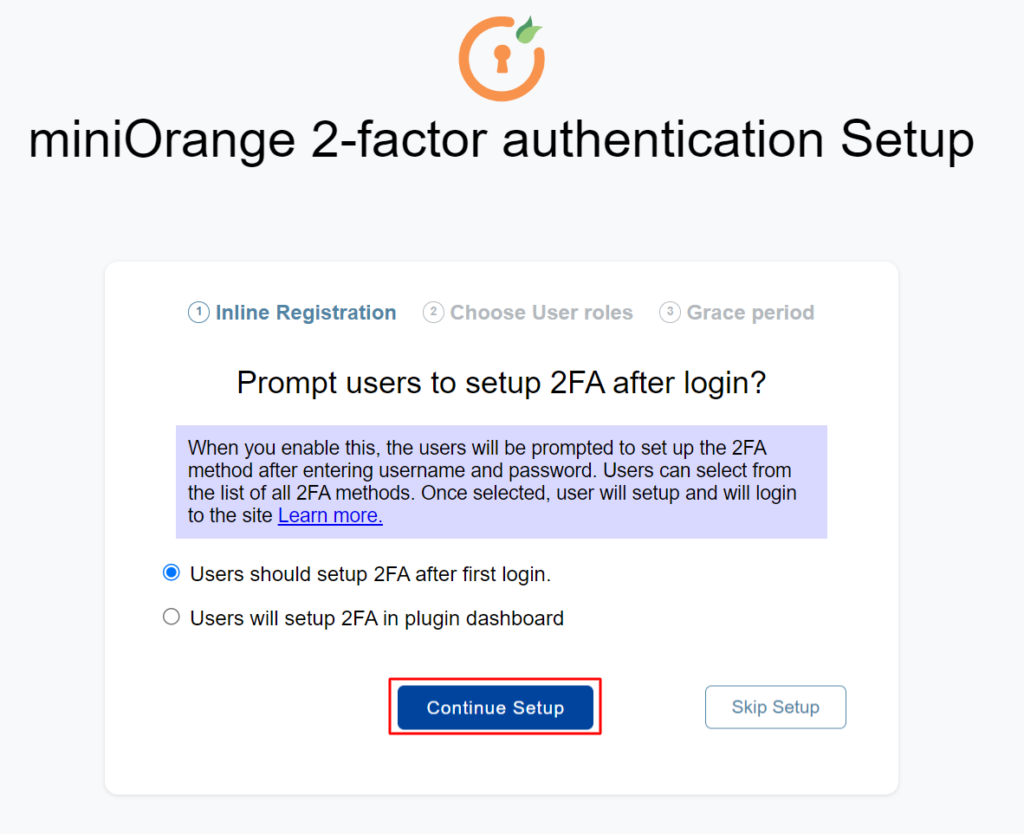
- 2. Select your 2FA option and click Continue Setup
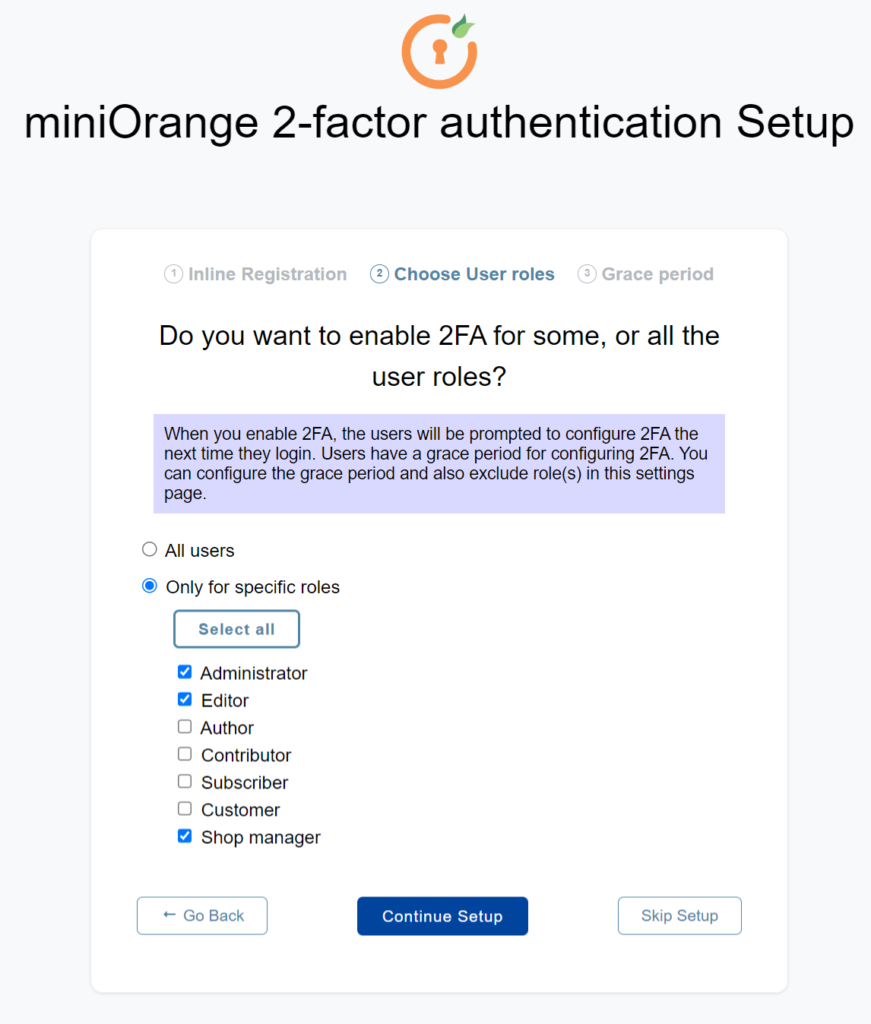
- 3. Select your user roles and Continue Setup
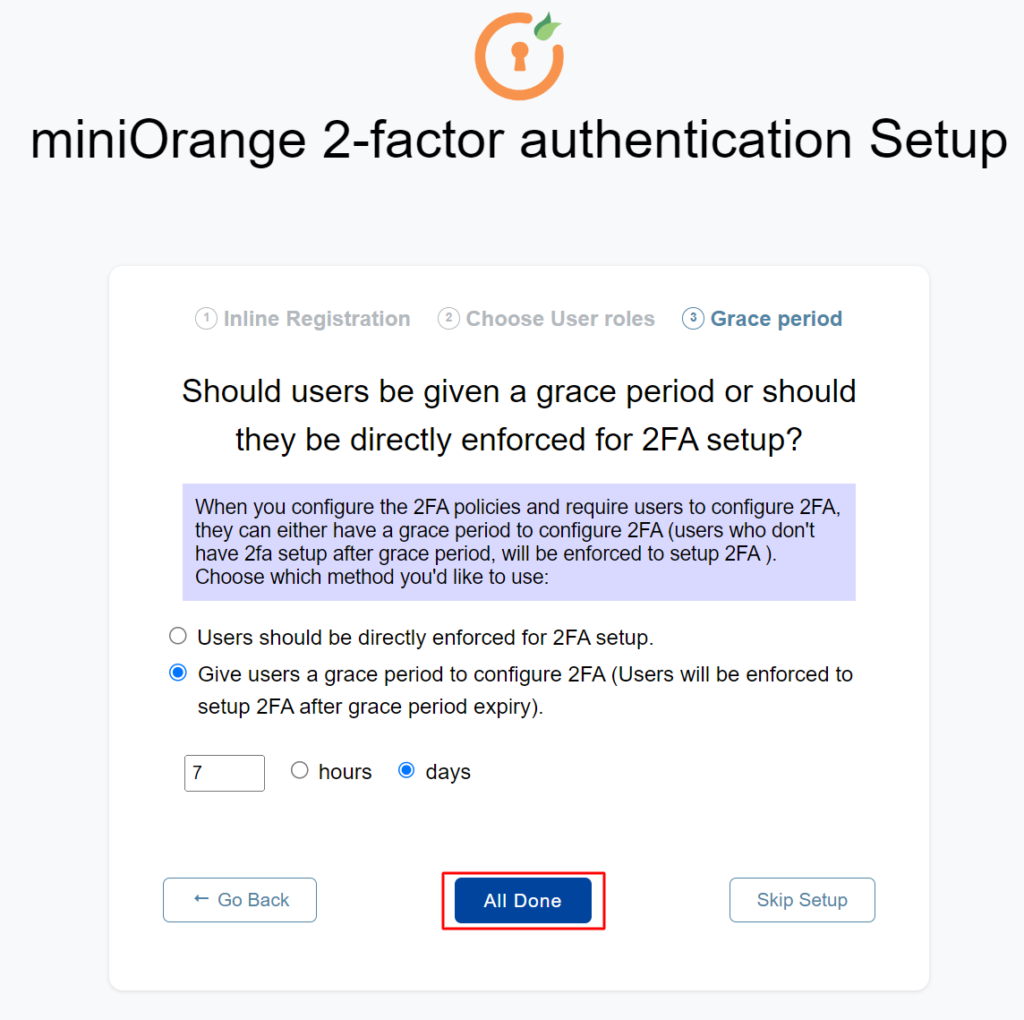
- 4. Select your 2FA enforce method and click All Done
If you don’t setup the setting using the setup method then you Go to your WordPress Dashboard -> miniOrange 2 Factor and you get Setup Wizard and your setting
SMS-Based Plugins
WP 2FA Plugin
- Install the WP 2FA Plugin:
- Navigate to
Plugins->Add Newin your WordPress admin dashboard. - Search for
WP 2FA. - Click
Install Nowand thenActivate.
- Navigate to
- Configure SMS-Based 2FA:
- Go to
WP 2FAsettings in your WordPress dashboard. - Select
Configurein theTwo-Factor Authenticationmenu.
- Go to
- Set Up Twilio:
- Create a Twilio account at
twilio.com. - In the Twilio console, obtain your
Account SID,Auth Token, and register a phone number. - Enter this information into the WP 2FA settings.
- Create a Twilio account at
- Enable 2FA for Users:
- Go to
Users->Your ProfileorUsers->All Users. - Scroll down to the
Two-Factor Authenticationsection. - Select
SMSas your 2FA method and enter your mobile number. - Click
Send Codeto verify the number. - Enter the code received on your mobile and click
Verify. - Save changes to your profile.
- Go to
Email-Based Verification
WordFence
- Install WordFence:
- In the WordPress admin dashboard, navigate to
Plugins->Add New. - Search for
WordFence. - Click
Install Nowand thenActivate.
- In the WordPress admin dashboard, navigate to
- Enable 2FA in WordFence:
- Go to
WordFence->Login Security. - Navigate to the
Two-Factor Authenticationtab. - Click
Activateunder the 2FA settings.
- Go to
- Setup Email Verification:
- Under the 2FA settings, select the
Enablecheckbox for email-based verification. - WordFence will send a one-time password (OTP) to your registered email during each login attempt.
- Make sure to save the settings.
- Under the 2FA settings, select the
- Testing:
- Log out and attempt to log back in. Check your email for an OTP to complete the login process.
Hardware Token
YubiKey
- Install Two-Factor Plugin:
- Go to
Plugins->Add Newin your WordPress admin dashboard. - Search for
Two Factor. - Click
Install NowandActivate.
- Go to
- Set Up YubiKey:
- In the dashboard, navigate to
Users->Your ProfileorUsers->All Users. - Scroll to the
Two Factor Optionssection. - Select
YubiKeyas your 2FA method.
- In the dashboard, navigate to
- Register Your YubiKey:
- Insert your YubiKey into a USB port.
- Click inside the
YubiKey Input Field. - Tap the YubiKey touch button to register it with your account.
- Save your profile settings.
- Testing:
- Log out and log in again. You’ll be prompted to use your YubiKey to complete the authentication.
Third-Party Services
Authy
- Install a Plugin that Supports Authy:
- For this example, you can use the
Authy for WordPressplugin. - Navigate to
Plugins->Add Newin the WordPress admin dashboard. - Search for
Authy for WordPress. - Click
Install NowandActivate.
- For this example, you can use the
- Create an Authy Account:
- Go to
authy.comand sign up for an account. - In your Authy dashboard, obtain your
API Key.
- Go to
- Configure the Plugin:
- In the WordPress admin, navigate to
Settings->Authysettings. - Enter your
API Keyand configure settings as per your requirements.
- In the WordPress admin, navigate to
- Enable Authy for Users:
- Go to
Users->Your ProfileorUsers->All Users. - Scroll to
Authy Settings. - Enable Authy and configure the mobile number linked with the Authy app.
- Save settings.
- Go to
- Testing:
- Log out and log in again. Open the Authy app to get the authentication code.
Each method for implementing 2FA on WordPress has its unique setup procedures, but all aim to provide an additional layer of security. Whether using Google Authenticator, SMS-based verification, email validation, hardware tokens, biometrics, or third-party services like Authy, you ensure your WordPress site stays protected against unauthorized access.
Remember, 2FA significantly boosts your security, but it’s crucial to keep backups of your 2FA methods (recovery codes) and to periodically review and update your security settings. This guide serves as a comprehensive resource to help you setup 2FA for your WordPress website, no matter the method you choose.
Conclusion
Implementing Two-Factor Authentication on your WordPress site is a critical step toward securing user accounts and sensitive data. Not only does it offer increased security, but it also ensures compliance with various regulations, protects against common cyber threats, and increases user trust. Whether you opt for an authenticator app, SMS verification, email-based 2FA, hardware tokens, or biometric verification, the additional layer of security is worth the initial setup and ongoing management.


